canis labs
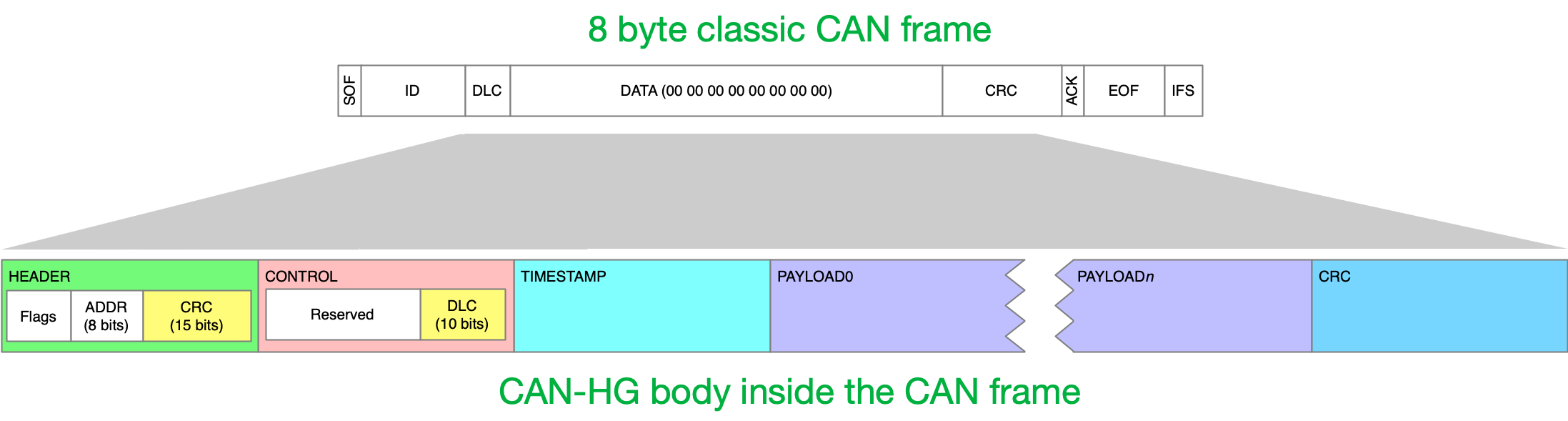
Canis Labs develops software, hardware and hardware IP technology for CAN bus, focused on security. It is the creator of the CAN-HG augmentation of classic CAN for adding performance and security while maintaining full compatibility with existing hardware and wiring, packing 276 bytes of payload inside an 8-byte classic CAN frame on a 250kbit/sec bus.
Our HQ is in the UK near Cambridge and we have offices in Switzerland and the US.
Canis Labs CTO Dr. Ken Tindell blogs about CAN and related technology at kentindell.github.io
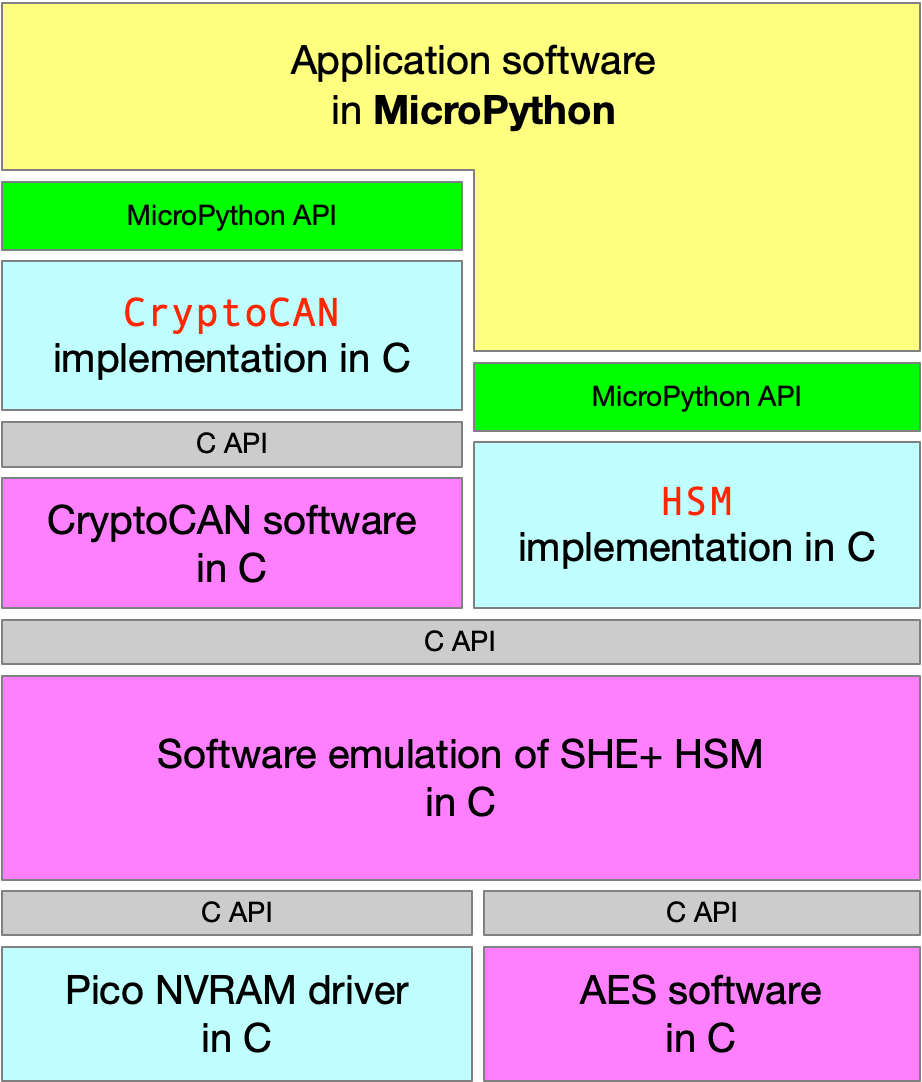
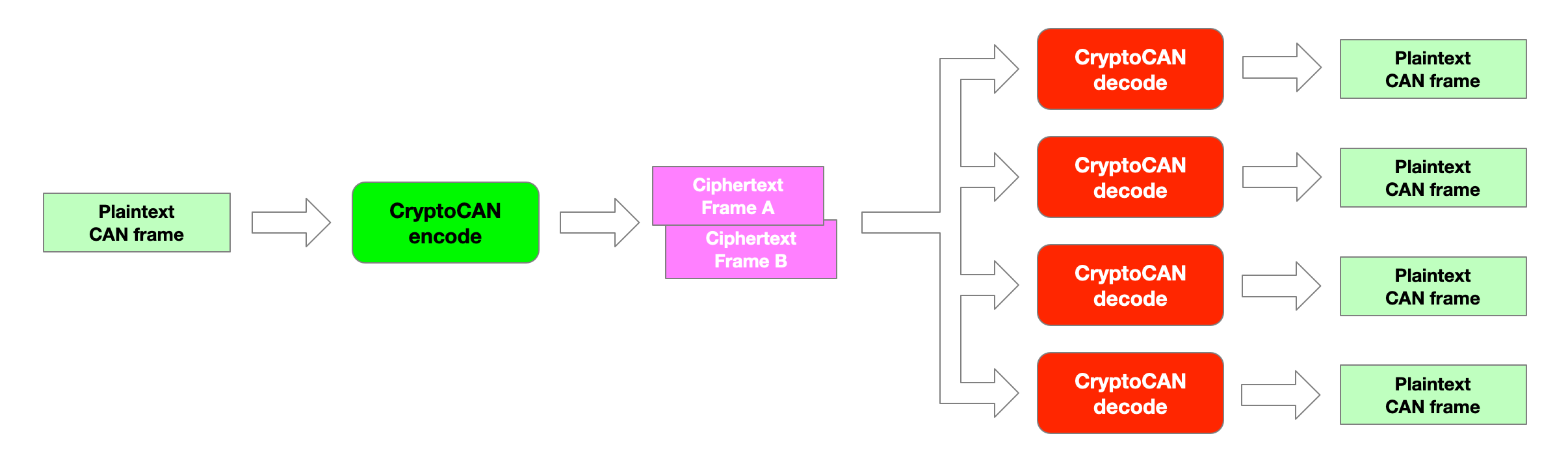
Canis Labs has released the CryptoCAN software stack for the Raspberry Pi Pico and CANPico board. It provides an API for an emulated SHE+ hardware security module and an API encrypted CAN messaging. MicroPython firmware with the CryptoCAN stack for the Raspberry Pi Pico and CAN APIs for the CANPico board can be downloaded for free.
Canis Labs CTO Dr. Ken Tindell gave a talk at Secure Our Streets 2022 (September 15, online) about using encryption on CAN bus. The slides for this talk are available. A recording of the talk, including the Q&A, is also available.
The CAN-HG protocol augments existing CAN with Higher speed data and provides bus Guarding support to stop spoofing and denial-of-service attacks. Most importantly, CAN-HG interoperates completely with existing CAN systems.
It is being evaluated by the United States Army Combat Capabilities Development Command (DEVCOM) Ground Vehicle Systems Center (GVSC) in a cooperative research and development agreement.
Canis Labs created the open source CANHack toolkit to demonstrate the viability of low-level attacks on the CAN protocol itself. A MicroPython version of CANHack is available for the CHV DEF CON 30 badge and the CANPico board.
The popular four-part Defending CAN video series explains how a CAN bus is attacked and gives different techniques for defending it. This first episode gives a taxonomy of attacks and shows how CAN protocol attacks work.
A CAN protocol attack is where the protocol itself can be attacked by malware sending carefully crafted signals to the TX pin of a CAN transceiver. How does malware get to control that pin? This short video explains how.
Priority Inversion is a common problem in priority-based systems, including CAN, and can lead to serious timing problems. This short video explains how. Our CTO Dr. Ken Tindell has also blogged about priority inversion and how it most famously happened on Mars.
Our CTO Dr Ken Tindell gave a seminar at the Automotive Security Research Group on CAN protocol attacks, demonstrating how they can be made by simple malware.