can security
CAN is a hugely successful fieldbus protocol that’s been around for more than three decades. It’s used today in hundreds of millions of devices including cars, trucks, buses, construction machines, ships, tractors, and spacecraft (there is even a CAN bus orbiting Mars). It has superb features that make it ideal for robust distributed real-time control, such as atomic broadcast. But one major drawback to CAN is that it has no security features and is vulnerable to all kinds of attacks, many that would have been inconceivable when CAN was created in 1986.
accessing can for an attack
The first step to any attack on CAN is accessing the bus. This attack surface can vary from physical access to the wiring and splicing in a device (used today to override emissions controls in trucks) through subverting wireless access points - not just Bluetooth or WiFi but also sensors for TPMS - to hijacking a device connected to CAN (most commonly a car’s infotainment system but ECUs and other control systems can be hijacked too).
types of attack
There are three properties of a secure system called the ‘CIA Triad’:
- Confidentiality: The message contents are secret
- Integrity: The message is genuine
- Availability: The system will continue to work
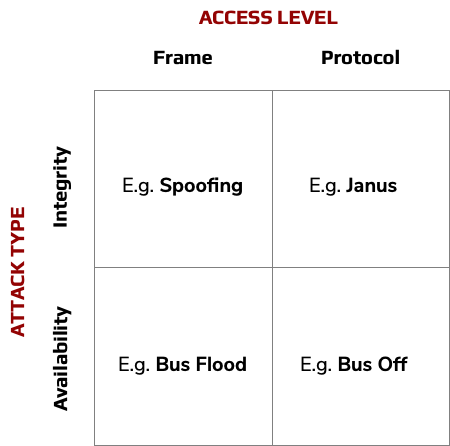
The two specific ways to attack a CAN bus are:
- Frame attacks: use a CAN controller to send valid CAN frames
- Protocol attacks: taking direct control of the CAN signal lines to the CAN transceiver and sending carefully timed pulses
Protocol attacks are far more insidious than frame attacks because they can force the system into unanticipated behaviours but also are less detectable. For example, the Janus attack sends different payloads to different receivers, and simply monitoring the bus will see only one of these. The Canis Labs CANHack toolkit is a software toolkit that demonstrates different CAN protocol attacks:
- Janus attack
- Frame spoofing (simple, timed and Error Passive variants)
- Error attack
- Double Receive attack
- Freeze Doom Loop attack
The CANHack toolkit is included in the MicroPython SDK for the CANPico board but it is also easy to make a CANHack board from breadboard.
Defending CAN bus
The classic ways to defend CAN bus are broadly:
- Encryption: add an authentication code to each message
- Intrusion Detection: spot traffic anomalies on the bus
- Security gateway: firewall off a risky bus and only forward legitimate traffic
The newest way to protect CAN is with hardware:
- CAN-HG: augment the CAN protocol for integrity and availability
The CAN-HG security protections are transparent to software, and use a central IDPS to monitor the bus and block an attacker’s access to the CAN bus at the hardware level.
White paper: Encryption on CAN bus: Overview of CryptoCAN (PDF). Discusses the special requirements for encrypting messages on CAN and gives an overview of CryptoCAN software and how it interfaces to hardware security modules.
White paper: CAN Bus Security: Attacks on CAN bus and their mitigations (PDF). A comprehensive overview of CAN security, covering how an attacker can gain access to the bus, the kind of attacks that can be mounted and the techniques that can be used to prevent such attacks (Version 07, issue date 2020-02-14, 39 pages)
GVSETS 2022 conference paper Defending Controller Area Network (CAN) buses (PDF) on the different types of attacks on CAN and techniques to defend against them, including details of CryptoCAN encryption on CAN and the CAN-HG augmentation of CAN for security.
White paper: CAN-HG overview: Augmenting Classic CAN for Performance and Security (PDF) white paper is a description of how CAN-HG augments classic CAN for much higher performance with security (Version 04, issue date 2020-12-14, 12 pages).
Episode 93 of the Autonocast podcast is an interview with Canis Labs' CTO Dr. Ken Tindell on augmenting CAN to meet the modern challenges of bandwidth and security.
The popular four-part video series Defending CAN, covering the topic of CAN security and going over the types of attack on CAN and the four major techniques for defending a CAN bus against those attacks.