canhack
The CANHack toolkit is a portable bit-banging library to emulate the minimal parts of the CAN protocol required for hacking a CAN bus. This toolkit is a proof-of-concept to show how various attacks on the CAN bus can be done purely in software if a microcontroller can be hijacked (we’ve not addressed how the hijacking could occur: it might be as simple as reflashing the firmware on an OBD-II dongle that an attacker owns, or something more complex like an exploit of a buffer overrun in a diagnostic messaging stack).
In most situations a microcontroller’s on-chip CAN controller is connected to a CAN transceiver and through this transceiver to the CAN bus. If the microcontroller can be hijacked then in general the pins allocated to the CAN controller can be re-purposed as GPIO pins. The CANHack toolkit has minimal assumptions about the environment, which are implemented in target-specific code that wraps the library. The basic requirements are:
- Access to CAN RX and CAN TX as GPIO pins
- Access to a timer to read the elapsed clock cycles (typically a free-running counter)
- Interrupts are disabled around key operations (the code spins on the timer waiting for events)
This can be ported to pretty much anything fast enough to bit-bang CAN (a Cortex M0 at 48MHz is probably too slow, but an ESP32 should be fast enough). The only other hardware requirement is that a CAN transceiver is connected to two GPIO pins.
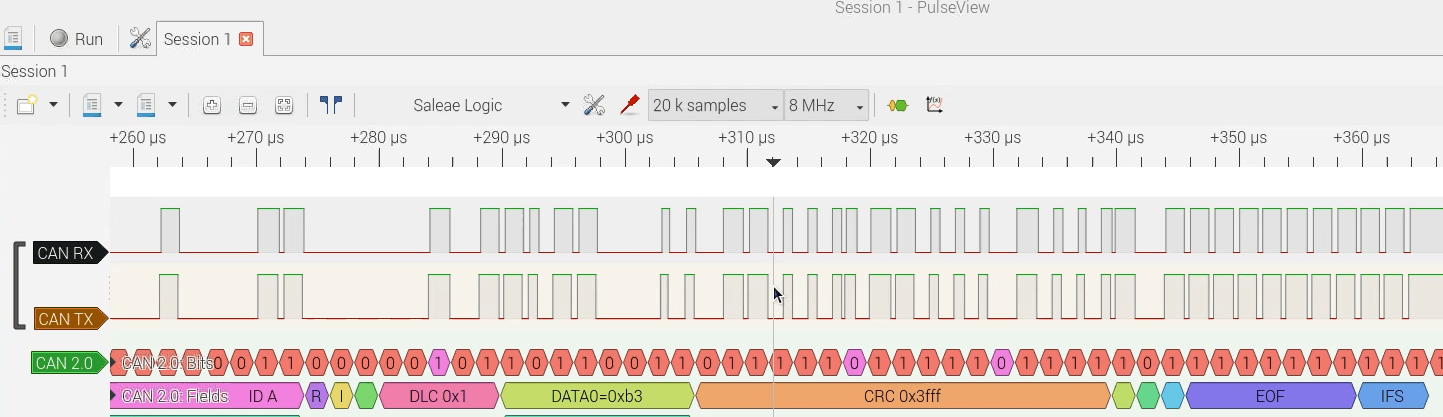
CTO blog post on using the CANHack toolkit to mount a new CAN protocol attack: the Janus Attack. This attack creates a single CAN frame contains two different payloads, so that a targeted device sees a different payload to other devices.
hardware
The Car Hacking Village badge produced for DEF CON 30 has a pre-built MicroPython firmware image for it with the CANHack API.
The badge can be bought from Intrepid Control Systems.
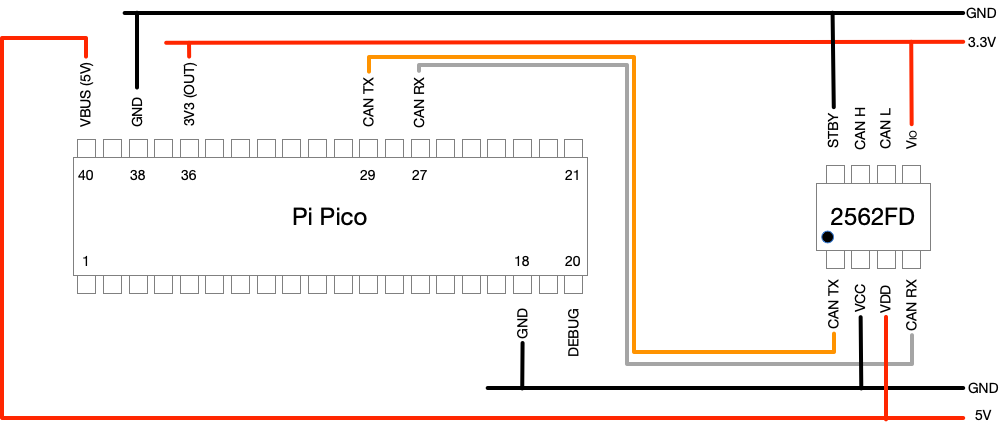
This CTO blog post shows how to use a Raspberry Pi Pico to make CANHack board using breadboard and a few components.
software

A cheatsheet for the CANHack Python API (also available in PDF).
CANHack MicroPython SDK Reference Manual covers the API for using CANHack from Python (PDF).
The Yes We CAN repository repository contains generic C source for the CANHack toolkit (in src) and also the MicroPython API to the toolkit (in pico/micropython).